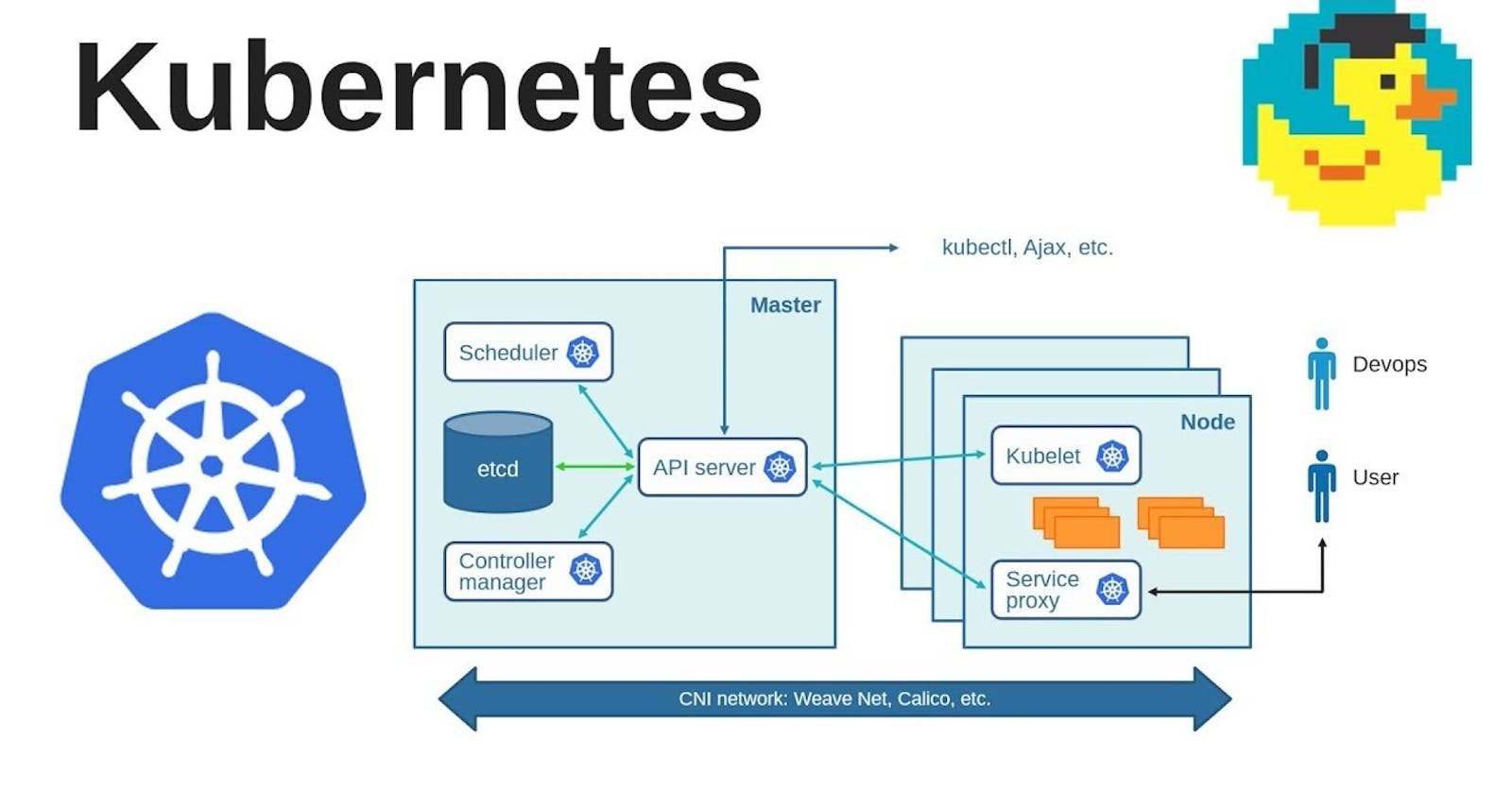
how would be provide security in kubernetes
Namespace:
Till date we are working on default workspace .
we have one hotel which has many rooms with different facility different-different sizes and every door has a different-different lock system that opens with a unique key. so why do they provide different facilities so that multiple different families stay with their requirements? Wherever they stay want complete isolation which gives a feeling of security. The qualities you get are according to the money you give and accordingly, they provide a room of different sizes and facilities.
On the whole, this hotel is like a Kubernetes cluster and the family is like IT/admin/user guys and management guys are k8s admin guys and if you want to set the limit of resources and security so minimum requirement is room. Here room acts as a namespace.
command to see namespace:
kubectl get namespace or kubectl get ns

To create namespace: kubectl create ns nameofnamespace


you can see that no resources are running on default namespace.
lets launch the pod with the namespace that we have created
manifest file for namespace


and when we launch the pod with mayateam namespace which I have created earlier , then the pod is created but when I checked it using kubectl get pods then it doesn't show me the pods because it shows the pods that is launched under default namespace.
To see the pods running in any namespace:
kubectl get pods -n namespacename

Security:

There are two ways of authentication
\>>>Password-based:-Manually enter username & password (as a human being we login with the password authentication
\>>>**Key-based authentication:-**In this program/tool/app for authentication ( when on behalf of human being some program, tool, apps login then they use key based authentication. we can't give the password to those program.
--> Different names of keys are private key, access, tokens, certificate, cookies.
\>>>first it hit the API server that is Kube API server they have own ip and port.
kubectl cluster-info

-->Whenever we run the kubectl command internally authentication happens again & again .
--> when you install minikube then automatically it install keys somewhere in windows and when you run kubectl command automatically it goes to the key file and authenticate itself .
like this Internet also works
Kubectl config view command tells us which cluster is connected, what username we are using for authentication & what key we are using for authentication


from one command we can manage the pods running in differnet system like in my own system , in another laptop, aws k8s, GCP K8s. By this kubectl command we can create the pods in mulitple cluster running on different os. Only thing we have to provide is ipaddress , port number in which cluster is running and password or key for authentication,
-->The context contains the username & IP address of the cluster
to see the context : kubectl config get-contexts

to see briefly use : kubectl config view

--> To make the client for the Kubernetes system minimum requirement is they should have connectivity
--> Few things required for making a client are
1. Client software
2. Client username
3. Client password
4. Server address
--> API server works as a gateway that collects the request from the client and sends the request to the internal programs
--> If we want to do authentication and instead of username & password we want to use key base authentication then there we have to use a certificate & the key

instead of username certificates are used and instead of password, key are used.
but in my context i am using minikube username see below

and certificate and key stored in this for authentication

how to configure any operating system (RHEL 9) as a client of k8s
checking connectivity

pinging with the minikube ip
now lets configure kubectl on rhel 9
cat <<EOF | sudo tee /etc/yum.repos.d/kubernetes.repo
[kubernetes]
name=Kubernetes
baseurl=https://packages.cloud.google.com/yum/repos/kubernetes-el7-\$basearch
enabled=1
gpgcheck=1
gpgkey=https://packages.cloud.google.com/yum/doc/yum-key.gpg https://packages.cloud.google.com/yum/doc/rpm-package-key.gpg
EOF
sudo yum install -y kubectl

Transferring key & certificate to the client Side through winscp


so now we have client.crt and client.key in rhel9
kubectl get pods --server url_of_server --client-key pathofkey --client-certificate pathofcertificate
let see whether it works or not

the error came is signed by unknown authority came
any client who want to use the certificate have to validate the certificate by the certificate authority .
so we have to transfer this CA certificate also in rhel9. lets find the path of CA (certificate authority)


so we have transfer all the required things for setting up the client
kubectl get pods --server url_of_server --client-key pathofkey --client-certificate pathofcertificate --certificate-authority pathofcertificate_authority

so if we delete all the pods from linux system then it should we deleted from the windows also lets check it

in windows

the only challenge in this we have to pass client key, certificate and certificate authority in doing anything like seeing running pods, deleting pods and so on which is overhelming in writing these longer command.
so for this role of config file came
how can we create config file
\>> for this we have to write the yaml file for config in linux side
kubectl config view > mayakube.config

this config file give us a facility to connect with multiple kubernetes cluster, users and servers. also we have do define which user is for which cluster. how do we know that this user uses particular cluster.


but if we again use view our configeration it again view null because we know we have created this file but kubernetes have no idea that which file we are using for complete configeration
for this we use: kubectl config view --kubeconfig filenameofconfig

now onwords we don't have to write these long commands only thing i have to write is config filename always.

but if you don't want to type this name of config file then kubernetes have a way for this
so whenever you run kubectl get pods then kubectl ( command) looking somewhere in home directory. In the homedirectory it see the folder called .kube . command go inside this folder and see the file with the name config file only and if it not find then we have to pass the file.
so for this copy the file and transfer to desired location
cp configfilethatyouhavecreated /root/.kube/config
we have to copy in this path only as kubectl command by default read this file

now you will do whatever like a windows.
so by this config file we can connect multiple client with multiple server. so we can make the multinode cluster with the help of this.
User Management:
kubeconfig file contains two things
\>>URL of the cluster IP address & port number
\>>Username & password of the user
Admin. config file gives unlimited power to the user

Cryptography has two types of key
-->Symmetric key:-Same key is used for locking & unlocking -->Asymmetric key:-Different keys are used for locking & unlocking
-->The public key & private key are used for encryption & authentication
\>>In encryption public key is used for encryption & private key is used for decryption
\>>In authentication private key is used for encryption & public key is used for decryption
so what we have to give to client is private key and certificate
and in the kubernetes side we need public key .
first login to minikube using mininkube ssh

then create the private key with name mayanksharma.key ( you can take your name)
openssl genrsa -out mayanksharma.key 1024

and save it in mayanksharma.csr file ( you can take your name)

a common name is used to uniquely identify the certificate

our requirement is to create the user and certificate
to create the certificate
firstly we have to fill the details which is CSR ( certificate sending request) this request is given to CA ( certificate authority) and it signed the certificate thats why it is called request.
secondly to give the final CRT certificate for you.
This certificate work like a final user and when we give key or password then user can connect to cluster through these credentials.
So if we want to create new user then we have to know Where the Certificate authority located so to locate it go to kube api server yaml file in which all detail are achieved about authentication as firstly authentication is happen there .
kube api server is located in `/etc/kubernetes/manifests/`
when the user login to kubernetes cluster it first hit the kube api server and it authenticate the user and it exist in

and if we see yaml file of kube-apiserver

ip that we are using is 192.168.59.113
and any client that want to login should have ca file that is highlighted below

we see that every service that we get are run in some pod like kube api server is running on pod with namespace kube-system let see

so ca file is located in /var/lib/minikube/certs/ca.crt

so every user CRT is signed by the ca.crt but this ca.crt is shared to every client so how could it verify that user CRT is signed by this certificate only . To verify it every ca.cert have it own private key.
if you want to sign the user CRT we use the private key of ca.crt.
creating the private key in /var/lib/minikube/certs/ca.crt
to create the key openssl genrsa -out mayank.key 1024

now creating CSR (certificate signing request)
openssl req -new -key mayank.key -out mayank.csr

using CA to sign CRT
openssl x509 -req -in mayank.csr -CA ca.crt -CAkey ca.key -out mayank.crt -days 365
this x509 is protocol is proved that this certificate is signed by some certificate authority

lets create the user in windows named mayank
transfer the keys and certificate in windows


transfer the key through winscp login minikube

create confige file from teh command line
kubectl config set-credentials mayank --client-ceritficate="c:\Users\mayan\.minikube\profiles\minikube\mayank.crt --client-key="c:\Users\mayan\.minikube\profiles\minikube\mayank.key"
then create the context file from this
kubectl config set-context mayalocal1 --user=mayank --cluster=minikube
now you can see the user using kubectl config view
and if you want to use this context as default cluster than
kubectl config use-context mayalocal1
so now onwords we launch the pod in this default namespace.
I hope you guys enjoys the blog do share and like it
want to connect with me 👇👇👇
My Contact Info:
📩Email:- mayank07082001@gmail.com
LinkedIn:- linkedin.com/in/mayank-sharma-devops